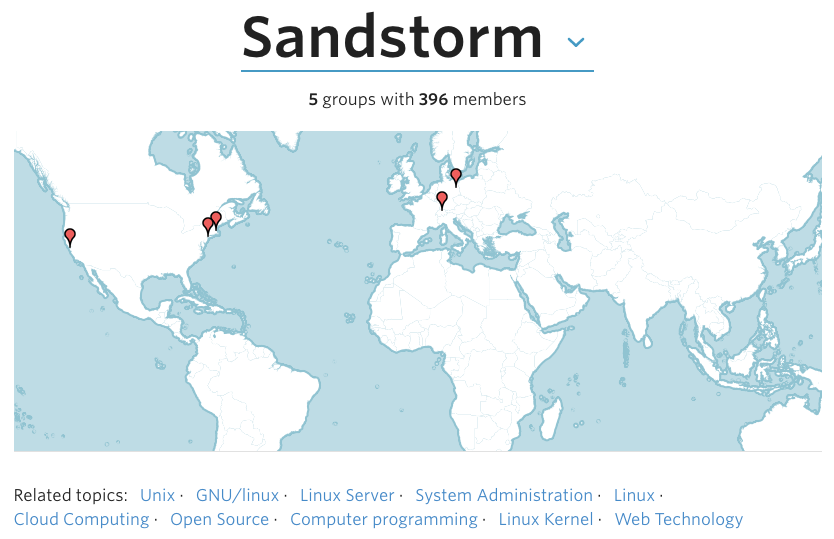
Upcoming Sandstorm meetups in SF, NY, Boston, Berlin, Zurich
By Jade Wang - 11 Jan 2016
Here in the San Francisco Bay Area, since May 2015, we’ve been organizing monthly Sandstorm meetups for community members can share their apps, works in progress, and learn from each other. Recently, Sandstorm community members have stepped up to organize local Sandstorm meetups in New York, Boston, Berlin, and Switzerland as well. Scroll to the bottom for the list of upcoming events:
To put your city on the map, drop a line to community@sandstorm.io, and I’ll get you all set up.
Upcoming Sandstorm events worldwide:
- Tue Jan 19, 2016 - Boston, USA - The Future of Sandstorm’s Powerbox UI (feat. Sandstorm core dev Drew Fisher)
- Wed Jan 20, 2016 - New York, USA - January Sandstorm NYC Meetup (feat. Sandstorm core dev Asheesh Laroia)
- Wed Jan 27, 2016 - San Francisco, USA - January Meetup with Lightning Talks
- Wed Jan 27, 2016 - Berlin, Germany - First Sandstorm group session Berlin (feat. Sandstorm core dev Asheesh Laroia, via Skype)
- Tue Feb 16, 2016 - Zurich, Switzerland - First Sandstorm Swiss Project Night
Sharing is referring - up to 30 GB bonus storage
By Asheesh Laroia - 18 Dec 2015
The easiest way to enjoy Sandstorm is on our managed hosting. Now, when you invite your friends to the service, you’ll get up to 30 GB of bonus storage as our way of saying thanks. When you share a grain with a friend, and they make an account and start sharing, that’s a referral.
How it works
You share a grain with a friend (who isn’t already an Oasis user).
Friend signs in.
Friend shares a grain with any person (including you), who successfully opens the grain.

Keeping track of your bonus
To see how you’re progressing, check out the referral program page in the top-right drop-down menu.
Or you can visit the referrals program page directly. Honestly, you should do that right now just to see Néna Nguyễn’s design work.
Paid subscribers can get up to 30 GB of free storage, in addition to the storage from their account level, 2 GB per person they refer. Free account holders can unlock unlimited grains and 50 MB of free storage per person they refer, up to 2 GB total. If you need even more space, you can always upgrade your account.
Common question: I received referral bonus storage for someone I don’t know. How does that happen?
Anyone who signs up for an Oasis account after opening up a grain that you shared counts as your referral. If you tweeted a link or shared a document on a mailing list (e.g., puzzle hunt team, collaborators at work, study group), anyone who found Oasis through you and signs up for an account counts as your referral.
Get started
That’s it! To get started, open any grain and click Share Access in the top bar.
7 community-driven Sandstorm presentations in 2015
By Jade Wang - 17 Dec 2015
As 2015 comes to a close, I’d love to give a big shout-out to the members of the Sandstorm community who have spoken about Sandstorm. Here’s a YouTube playlist of the ones that we have videos of:
- Jack Singleton, author of HackerSlides and lead dev on SandForms, spoke at Chaos Communication Camp, and organized a Sandstorm booth at the Digital Rights in Libraries Conference.
- Audrey Tang, author of EtherCalc, gave a lightning talk at Ignite Open Data and also created a Chinese version of the speaker kit.
- Jon Spriggs spoke about Sandstorm at Oggcamp.
- Jeff Mendoza gave a lightning talk at GopherCon.
- James Cyrus, host of GeekblogTV, produced this tutorial on installing Sandstorm on your Digital Ocean droplet
- Jake Weisz, who packaged many apps and is super helpful in answering community questions on sandstorm-dev, spoke at the Chicago GNU/Linux Users Group as well as Open Source Open Mic.
- Deb Nicholson and Chris Webber (of MediaGoblin) gave a Sandstorm demo during their FOSDEM talk (Sandstorm demo starts at 24:57).
I made this list based on the page on the wiki. If you also gave a talk about Sandstorm this year and are just now adding yourself to the wiki, drop me a line at community@sandstorm.io, and I’ll update the post to include you. A huge thanks to everyone who has given a talk, as well as the folks in the brigade who show up everywhere on Hacker News, reddit, and request coverage of Sandstorm on the Linux Action Show. I heart all of you. If any of you happen to live in or travel through the SF Bay Area, you should share your work at a Sandstorm meetup or at least drop by.
Here are some ways to get involved in the community:
-
Start a local Sandstorm meetup and spread the love: drop a line to community@sandstorm.io and let me know where you are.
-
Give a Sandstorm talk at a local meetup or hackerspace or your work place: check out this speaker kit, and add your talk to the list.
-
Subscribe to the shiny new Sandstorm YouTube channel
Stay tuned for App Market highlights of 2015!
Authenticated app packages on Sandstorm with PGP and Keybase
By Drew Fisher - 12 Nov 2015
I like to joke that Sandstorm is a security project posing as a usability project. In actuality, it’s both! Sandstorm users deserve to be confident that the apps they’re running are exactly as the packager built them, and have not been backdoored or accidentally modified by a malicious ISP, government, or other attacker. Furthermore, this information must be easy to consume and verify.
To that end, I’ve worked with Kenton to make it possible to provide a cryptographic chain of trust that connects the app package you’re installing to the app publisher’s online accounts. When you install the EtherCalc spreadsheet app, Sandstorm lets you see that the app was made by the same Audrey Tang that owns audreyt on Github and au on Keybase. Publisher information is shown front and center:
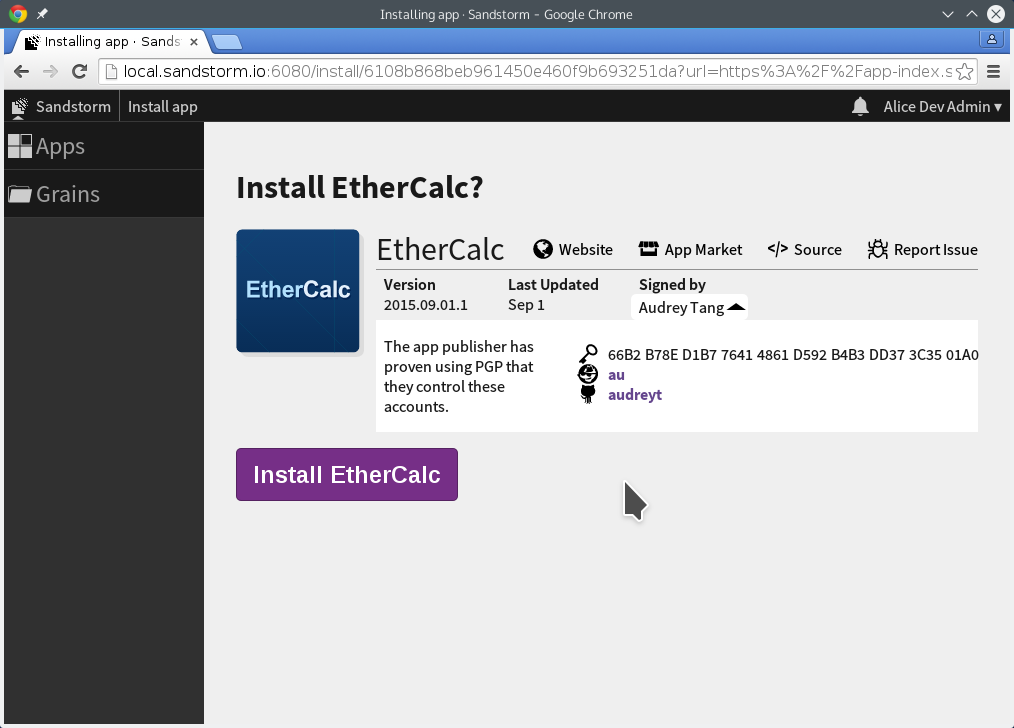
To make this all work, there are a few steps involved.
The app ID is a public key
Sandstorm has required that apps be signed since its inception, providing a first line of defense against package corruption. The app is signed with an app-specific Ed25519 key at package-building time. Sandstorm uses the public key as the app’s ID on the app market and your server.
This guarantees that app packages cannot be modified by a CDN or the app market without using a different app ID. This also had the nice effect of providing trust-on-first-use properties for apps until we were able to bind these identities to something more meaningful. The upshot: when you’ve installed an app, only the same app author can provide updates to it.
Connect the app ID to a PGP key
Since the release of the app market, app packagers have been PGP-signing statements that they are the author of the Sandstorm app with that app ID, and include that statement, their PGP public key, and the email address associated with that key in their package’s metadata. Since that metadata is in the Sandstorm package file signed by the Ed25519 key, any server running Sandstorm can verify that these statements were provided by the person or people who control that Ed25519 key. Additionally, since the statement is signed by the PGP key, there is a trust path from the owner of that PGP private key to the app you are installing. To defeat this, an attacker would need to convince an app author to replace both their signing statement and their PGP key in the package metadata with ones produced by the attacker.
Connect the PGP key to social identities
The next goal is to connect that PGP fingerprint to meaningful, real-world identities. While a handful of people might be able to rely on the web-of-trust to verify PGP fingerprints, most users will need something more approachable. That’s where Keybase comes in. Keybase helps you link PGP keys to social identities, like GitHub or Twitter accounts. App authors can create a Keybase account, then create signed proofs-of-ownership that they post to their social media pages or websites. Keybase provides an index of these proofs, so given a PGP fingerprint, you can list the accounts for which the PGP key’s owner has proven control.
The result: end-to-end verified apps
When you go to install a package, Sandstorm verifies that the package is correctly signed by the Ed25519 key. It looks for a PGP signature in the metadata, and verifies that the PGP-signed assertion is for the correct app ID and the email address specified in the metadata. It queries the Keybase API to see what accounts the packager has proven ownership of, and lists them with their links on the app install page.
Currently, the implementation of this feature trusts Keybase’s servers to verify proofs and return an accurate list of the signer’s identities. However, Keybase proofs are designed to be verifiable by third parties without trusting Keybase, and we plan to extend Sandstorm to do this, thus eliminating Keybase itself from the trust chain.
So that’s how Sandstorm links app packages to their creators’ social identities, with cryptographic verification at each step along the way, with no additional action needed by end users. This is software authenticity that Just Works, and it’s available today for all Sandstorm users and packages in the App Market. Today is a good day to install Sandstorm on your own server or sign up for our managed hosting.
Graphics and one-click installers for everyone
By Jade Wang and Asheesh Laroia - 10 Nov 2015
Open source web app developers build great apps. But sometimes, backend-minded developers need a little help, from making it easy for end users to install their apps to making their icons and other graphics visually appealing. To make open source web apps viable as an ecosystem, the apps must be easy to install and use, and to get the attention they deserve, they should have good-looking icons that convey the purpose of the app.
Graphics for everyone
Lately, we’ve been running an experiment – will app authors be interested in custom graphics, designed by Néna Nguyen at Sandstorm? So far, the response has been positive!
So I’m excited to announce we’ll do this for everyone who packages their app for Sandstorm: To support app authors, we are happy to help with graphics. This is on top of the one-click install for your app that Sandstorm enables, which works just as well in the cloud as it does for self-hosters (see below). For instance, Néna will make an icon for you if you need it. Check out this awesome icon set that Néna made for Wekan (kanban board):
Wekan (open source Trello alternative) icons in varying contexts. Check out Wekan on the App Market »
One-click installers for everyone
An app written using Meteor is the easiest to package – there’s a special tutorial for Meteor apps. If you input the URL of your GitHub repo below, we can even do a first-run of the packaging for you and ping you with a live demo featuring your own spk (Sandstorm package):
Meteor or not, any web app that runs on Linux can be packaged for Sandstorm. Get started with this documentation link.
Drop a line to community@sandstorm.io with any questions and we’ll make sure you succeed.